There'll be particular periods in the course of a take a look at cycle that CyberRatings will publish personal test studies in advance of a Comparative Report is produced.
Cybercriminals exploit vulnerabilities in details-driven programs to insert destructive code into a databased by using a malicious SQL statement. This provides them use of the sensitive information contained while in the databases.
Cloud protection is a phase of IT that promotions with managing threats and issues with a cloud-dependent community. In addition, it involves discovering and utilizing solutions, mostly wirelessly.
Password attacks: Password cracking is The most prevalent methods for fraudulently getting procedure obtain. Attackers use numerous methods to steal passwords to accessibility personalized information or sensitive data.
A highly effective TPRM application is similar to the ‘north star’ that guides hazard management across your organization, uniting each touchpoint less than one particular widespread purpose: figuring out which third get-togethers introduce by far the most chance, and lowering it prior to it results in measurable hurt.
As an example, spyware could capture charge card particulars. · Ransomware: Malware which locks down a consumer’s files and details, with the specter of erasing it Unless of course a ransom is compensated. · Adware: Promoting software program which can be utilized to unfold malware. · Botnets: Networks of malware contaminated pcs which cybercriminals use to perform jobs on-line with no user’s permission. SQL injection
Security ratings are a wonderful metric for simplifying stability posture and possibility exposure. Consider providing cybersecurity reports and graphical representations of your safety posture (including your safety rating after some time) on your board to help members immediately detect and realize TPRM principles and techniques.
I commend the vendors from the Cloud Network Firewall examination whose stability proved powerful. They have demonstrated how TPRM properly their products and solutions conduct underneath rigorous screening circumstances.
52 percent of companies think that EERM is popping into a broader notion that features deal management, efficiency administration, and monetary administration
使用硬件和软件来监控、检测和控制工业系统变更,全方位保护关键基础设施。
A better check out some of these 3rd party risk administration problems can lose mild on why TPRM programs are Specially important nowadays.
Examine how Have faith in Exchange is revolutionizing the safety questionnaire course of action, liberating security groups with the stress of repetitive, guide duties.
If cybercriminals infiltrate this credit card processor, your purchaser’s info can be compromised, resulting in economical and track record outcomes for the Group.
A few of these sectors tend to be more pleasing to cybercriminals mainly because they collect monetary and health care facts, but all businesses that use networks may be focused for buyer details, company espionage, or purchaser assaults.
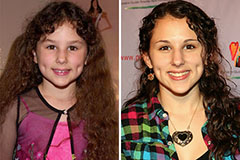 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Val Kilmer Then & Now!
Val Kilmer Then & Now! Lynda Carter Then & Now!
Lynda Carter Then & Now! Samantha Fox Then & Now!
Samantha Fox Then & Now! Ryan Phillippe Then & Now!
Ryan Phillippe Then & Now!